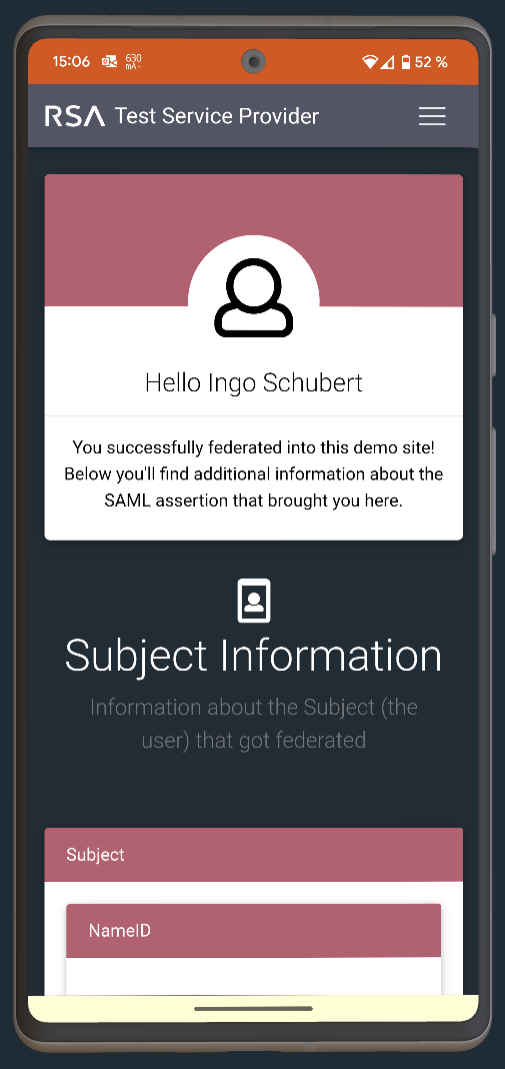
Simple Test Service Provider
This site is a SAML 2.0 service provider. It does not implement the entire
SAML 2.0 specifications but only as much as is needed to parse an incoming assertion and extract information out of it and display it.
The advantage of this site is that you do not need to register or otherwise make it trust your Identity Provider.
It simply trust everyone... it's suitable for demonstration purposes only!
What does this site do?
If you are wondering why you would use this site, here are some of the problems we are trying to solve:
Testing an IDP
If you setup a SAML Identity Provider you may want to quickly check if it works correctly.
This site helps you with that task:
Point your IDP to this site (see instructions) and test away!
Demo
You have a demo IDP with all kinds of cool authentication methods and policies ("Hello RSA ID Plus!") and need to show it's capabilities... this site is an excellent target application!
What does this site do exactly?
Still confused? Here is some more detail:
After receiving a SAML assertion to the Assertion Consumption Service (ACS) URL, the SAML assertion is parsed and the results are displayed.
IDP initiated SSO and SP initiated SSO are supported. Please see the instructions on how to setup both variants.
The protected part of this site is only accessible after you federated into this site.
This site trusts all IDPs - there is no need to upload your IDP metadata or any IDP certificate if you just like to see IDP initiated SSO working.
This universal trust is done by simply trusting all IDP entityIDs and certificates. This isn't a secure site - it's a test and demo site.
Some of the features supported
IDP initiated SSO
Your IDP sending a unsolicited SAML Assertion and this site consuming it.
SP initiated SSO
This SP sending a SAML AuthNRequest to your IDP which will send a SAML response back to this site.
Requesting a specific authentication method or policy from an IDP
This is done by setting the AuthenticationContextClassRef in the Authentication Request.
Displaying Attribute statements
If the SAML assertion contains an attribute statement, all the attributes will be displayed.
Displaying Authentication details
If it is in the SAML assertion, the authentication context class and other information about the authentication done at the IDP will be displayed.
Requesting authentication for a specified user
With this, the IDP will see that the SP (this site) already did identify the user and therefore can concentrate on e.g. strongly authenticating the user.
Stuff that won't work
Sending signed AuthNRequests
While we are not ruling out that this will work in the future, it's not supported at the moment.
Receiving encrypted SAML assertions
That's not even on our radar...
While this list isn't complete, don't worry too much: we support the common SAML features so in 99% of all cases using this site for SSO demos is working just fine.
Contact us
Have a suggestion? Need help?